10:00
6
min at reading ▪
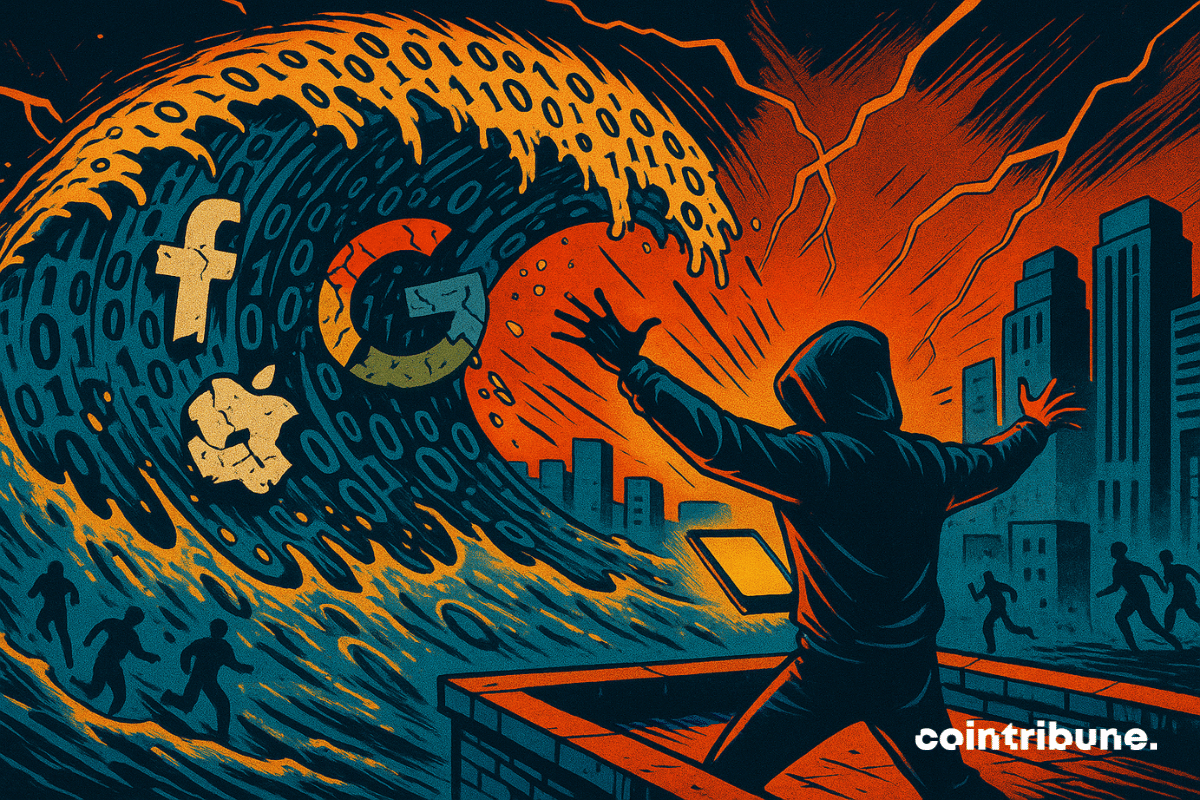
The story is written under tension, but against the tide. While the bombs shook the Middle East, the next queue is bait: internet. Has just exposed a digital earthquake 16 billion data on identificationAccording to Cybernews. Among them access to AppleGoogle, Facebook … nothing discreet. Passwords, cookies, complete session, delivered to pasture. It’s no longer a defect, it’s a collapse. Furtive space time is over. Here is the age of mass digital looting.


In short
- Massive leakage reveals 16 billion identifiers stolen through malicious software called Infostealers.
- This data includes access to Apple, Google, Facebook and many other sensitive digital services.
- The files were found on unsecured cloud servers, temporarily accessible to scientists.
- This data flight technology also threatens crypto, e -maly and professional networks.
Immersed in the largest digital bloodshed ever organized
There are hacks that shaken fintets such as Bybit and its $ 1.4 billion evaporated. But what Simmers in the shadow of recent revelations could go through this bleeding for simple scratch. By Cybernews, 30 data files were identified, each contained up to 3.5 billion identifiers. For comparison, this represents two identifiers on a person on Earth. Scientists evoke dEscapes from malicious software, especially infostealersCable to suck everything you write, click or save.
Each line of these bases contains URL, identifier, password. This opens the door to Apple, Facebook, Google, Github, government portals. Hackers were not introduced directly with these giants. However, great identifiers allow you to enter, without an accident, by circumventing walls with the most common approach: your session already open.
As Mario Nawfal explains:
It is not a simple escape. It is a plan for mass exploitation.
And the damage was not over. New bases appear every week. The threat is active. Alive. And she learns.
Technology on theft of theft: When ingenuity becomes poison
What makes this flight particularly dangerous is Technology used to build data. Cybernews scientists have found Bases hosted temporarily on unsecured storageas elasticsarch or cloud objects. No sophisticated hack here: just negligence, error in the organization.
One of the data sets had the name associated with a telegram, another with Russia. One of them contained 455 million identifiers. Cookies and authentication chips were also present. Clear, Some hackers have access to your accounts even if you change your password. And all services automatically reset cookies.
The technology is a double weapon. It facilitates communication, exchange, innovation. But in the wrong hands he becomes an accelerator of the disaster. Experts speak of a change in the era in the world of cyber attacks: we leave telegram groups for centralized bases, ready to use on a large scale.
One of the most significant quotations of the survey is this, signed Cybernews:
It is not just an escape – it is fresh and usable intelligence on a large scale.
Cold clinical sentence. It summarizes thatthe logic of computer crime that has become an industrial.
Crypto, e -mail and nets (Facebook, Apple, etc.): No one is immune to technology
If web giants are shaking, the crypt community. Developers, merchants, dapps All rest on a safe access. And most go through the same login as everyone: Google, Facebook, Github. Just say that the keys to the web3 were just dropped on the street.
Even safety initiatives in blockchain, such as decentralized authentication, try to compete with this massive attack. Grka’s reaction to Tweet Satoshi Club clearly evokes the range of this leak: This violation applies to Apple, Google and Github. And therefore the crypto universe Ricochet.
Here’s what you should remember:
- 30 exposed data files, some of which have never been seen before;
- On average 550 million identifiers per game;
- Information present: login, password, cookie, URL;
- Presence of tokens of the session circumvention 2FA;
- The bases point to the cloud, VPN, forums, e-mails, github services.
The consequences are systemic. The technology used to ensure the approach itself becomes a vector of vulnerability. It is Brutal interrogation For the whole ecosystem.
With 16 billion stolen data, it seems that the Coinbase affair, which concerned almost 70,000 victims last May, is almost unofficial. However, it was enough to call for a ransom and the leak of trust. Imagine what 16 billion digital entrance doors can cause in the hands of bad players. Technology is developing rapidly. Also cyber criminals. This time the battle is played quietly … and for air.
Maximize your Cointribne experience with our “Read to Earn” program! For each article you read, get points and approach exclusive rewards. Sign up now and start to accumulate benefits.
Blockchain and crypto revolution! And the day when the impacts will be felt on the most vulnerable economy of this world, I would say against all hope that I was there for something
Renunciation
The words and opinions expressed in this article are involved only by their author and should not be considered investment counseling. Do your own research before any investment decision.